Did you know that an expired SSL certificate can bring down your entire production system, costing companies thousands in lost revenue and reputation damage? For DevOps and IT admins, proactive solutions to monitor SSL expiry are no longer optional—they're critical to prevent security warnings that drive away users and create unnecessary emergency work.
1. Introduction
Did you know that an expired SSL certificate can bring down your production system, costing companies a huge $$$ in downtime?
SSL certificates are essential for ensuring secure communication and maintaining system reliability. However, expired or misconfigured certificates can result in:
- Revenue Loss
- Reputation Damage
- Wasted Time and Resources
- Security Risks
These challenges underscore the critical need for SSL certificate monitoring and uptime monitoring to protect business operations and optimize resources effectively.
For DevOps and IT admins, proactive solutions to manage and monitor SSL expiry are no longer optional—they are critical. Manual monitoring can be error-prone and time-consuming, leaving organizations vulnerable to costly incidents.
This article explores why SSL monitoring is critical, how to proactively prevent SSL-related incidents, and the best CLI tools to manage SSL certificates.
2. What is SSL and Why SSL Issues Are Critical?
What is SSL?
SSL (Secure Sockets Layer) is a standard security technology that establishes encrypted connections between web servers and browsers, ensuring that data transmitted remains private and secure.
SSL certificates serve as a digital guarantee that a website is authentic, encrypted, and secure for users, making them a cornerstone of online communication.
Why SSL Issues Are Critical?
SSL issues, such as expired or misconfigured certificates, can have impacts on businesses, affecting revenue, reputation, operational efficiency, and data security. Here’s how:
Revenue Loss:
Expired SSL certificates can cause system downtime, making websites or APIs inaccessible. For e-commerce platforms, even minutes of downtime during peak sales can result in significant revenue loss and missed business opportunities.
Reputation Damage:
Users encountering browser warnings like “certificate expired” or “connection not secure” may lose trust in the brand. Negative experiences spread quickly, tarnishing the company’s reputation and driving customers to competitors.
Wasted Time and Resources:
IT teams often spend hours troubleshooting SSL-related issues, diverting resources from critical projects. Without proper SSL certificate expiry monitoring, resolving expired certificates becomes a time-consuming and repetitive task.
Data Security Risks:
Misconfigured or expired SSL certificates expose systems to potential attacks, such as data interception or phishing. These breaches can compromise sensitive information, resulting in compliance penalties and loss of user trust.
Real-life SSL outages
One notable example is Starlink, a satellite internet constellation operated by SpaceX, which experienced severe downtime for several hours on April 8. Users from Melbourne to Seattle reported issues caused by SSL-related disruptions.
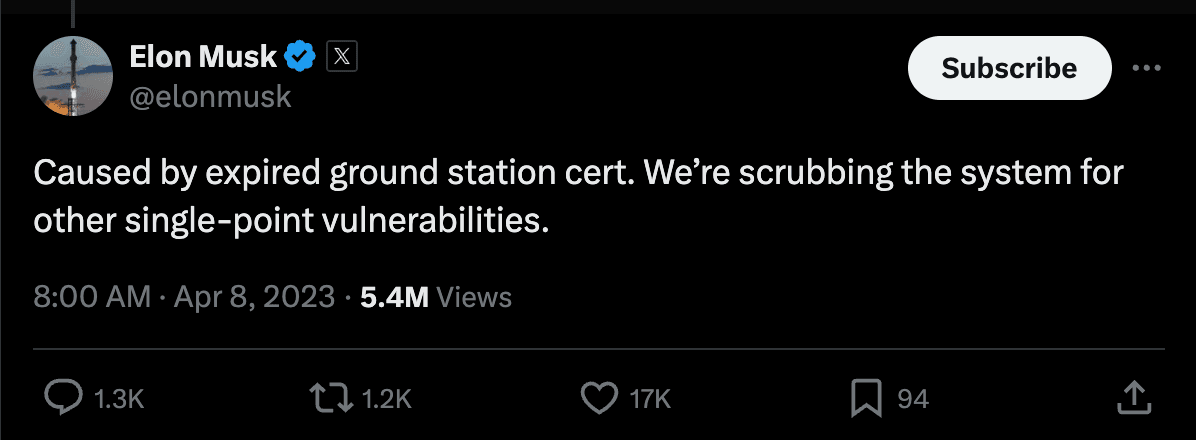
Impacts Starlink Faced:
- Reputation Damage: Negative feedback quickly spread across forums and social media, amplifying dissatisfaction and tarnishing the brand’s credibility.
- Wasted Time and Resources: Starlink’s technical teams had to divert significant time and resources to diagnose and resolve the issue, pulling focus away from strategic initiatives and future improvements.
3. Best practices for SSL monitoring
Effective SSL monitoring ensures your systems remain secure, available, and compliant. Here are the best practices to follow:
- Continuous Uptime Tracking: Implement downtime monitoring tools to detect and respond to system interruptions swiftly
- Regular Validation: Periodically check SSL certificate validity and configuration across all environments, including production and staging.
- Automated Alerts: Set up proactive reminders for SSL certificate expiry monitoring to avoid last-minute renewals.
- Integrate Monitoring into DevOps Workflows: Use CLI tools and scripts to automate the process, ensuring seamless management.
Following these best practices helps keep SSL certificates valid and secure, but manual checks are time-consuming and error-prone, especially with multiple certificates.
SSL CLI tools provide solutions for efficient validation, monitoring, and management. Here are the most effective tools for SSL certificate expiry monitoring and validation.
4. What Are the Best CLI Tools for SSL Certificate Expiry Monitoring and Validation?
CLI tools offer a powerful way to manage and validate SSL certificates, providing flexibility and automation for DevOps teams. Here are some of the most effective tools for SSL certificate monitoring:
OpenSSL
OpenSSL is one of the most versatile tools for managing SSL certificates. It can be used to generate, validate, and inspect certificates, making it a cornerstone for SSL certificate monitoring.
Common CLIs
Check certificate details, including issuer and expiration date:
openssl x509 -in certificate.pem -noout -text
Retrieve the expiration date of a certificate from a live server
openssl s_client -connect [bubobot.com:443](<http://bubobot.com:443/>) 2>/dev/null | openssl x509 -noout -dates
notBefore=Nov 12 13:32:42 2024 GMT
notAfter=Feb 10 13:32:41 2025 GMT
Command to Test Supported Ciphers
openssl s_client -connect [apple.com:443](<http://apple.com:443/>) -cipher AES128-SHA
CONNECTED(00000005)
depth=2 C = US, O = DigiCert Inc, OU = [www.digicert.com](<http://www.digicert.com/>), CN = DigiCert Global Root G3
verify return:1
depth=1 C = US, O = Apple Inc., CN = Apple Public EV Server ECC CA 1 - G1
verify return:1
depth=0 businessCategory = Private Organization, jurisdictionC = US, jurisdictionST = California, serialNumber = C0806592, C = US, ST = California, L = Cupertino, O = Apple Inc., CN = [apple.com](<http://apple.com/>)
verify return:1
Advantages:
- Versatile and widely supported.
- Allows detailed inspection of SSL certificates, including expiration, issuer, and supported ciphers.
- Open-source and free to use.
Disadvantages:
- Requires advanced knowledge of command-line operations.
- No built-in automation for monitoring or alerts; manual setup is needed for proactive expiry tracking.
SSL-Cert-Check
A CLI tool designed specifically for monitoring SSL expiry and automating alerts.
Check Expiration Date of a Single Certificate Use the -f flag to specify a certificate file:
ssl-cert-check -f /path/to/certificate.pem
Check Expiration for Multiple Certificates Use the -d option for domain-based checks:
/opt/ssl-cert-check -s apple.com -p 443Host Status Expires Days
apple.com:443 Valid Feb 12, 2025 74
Set Expiry Threshold Alerts Trigger alerts when certificates are nearing expiry:
/opt/ssl-cert-check -s apple.com -p 443 -x 30Host Status Expires Days
apple.com:443 Valid Feb 12, 2025 74
Automate Checks with Cron Jobs Schedule periodic checks and receive automated notifications:
0 9 * * * /opt/ssl-cert-check -s apple.com -p 443 -x 30
Advantages:
- Purpose-built for SSL certificate expiry monitoring.
- Includes automated alerts for expiring certificates.
- Simple to integrate with cron jobs for periodic checks.
Disadvantages:
- Limited functionality outside of expiry monitoring.
- Requires installation and configuration, which can be less intuitive for beginners.
Certbot
An essential tool for automating the issuance and renewal of SSL certificates, especially for Let’s Encrypt.
Request a new certificate:
certbot certonly --standalone -d bubobot.com
Requesting a certificate for bubobot.com
...
Renew existing certificates:
certbot renew
Processing /etc/letsencrypt/renewal/bubobot.com.conf
Certificate not yet due for renewal ...
Advantages:
- Ideal for automating the issuance and renewal of SSL certificates, especially with Let’s Encrypt.
- Simplifies renewal processes, reducing the risk of expired certificates.
- Highly automated, saving time for DevOps teams.
Disadvantages:
- Focused on Let’s Encrypt, which may not suit all organizations or certificate authorities.
- Requires initial setup and configuration that may be complex for smaller teams without experience.
5. Conclusion
SSL certificate monitoring ensures secure communication, prevents costly downtime, and protects user trust. Expired SSL certificates can disrupt operations and leave systems vulnerable to attacks, making proactive monitoring a must-have.
By automating SSL monitoring and setting up alerts, DevOps teams can focus on strategic tasks instead of manual checks. A robust workflow with tools like CLI scripts and monitoring platforms reduces the risk of missing critical renewals.



